Data Integrity Check
 SecurDisc provides another layer of protection through its Data Integrity Check, which warns you if the data on a disc is at risk of disc decay, giving you time to back it up to another disc.
SecurDisc provides another layer of protection through its Data Integrity Check, which warns you if the data on a disc is at risk of disc decay, giving you time to back it up to another disc.
This is accomplished by using the checksum feature. As another core security feature, Data Integrity Check is always enabled and cannot be disabled.
Checking Data Integrity Easily
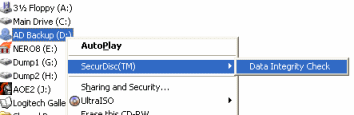 The easiest way to check Data Integrity is simply to go to My Computer and right click on the drive with the SecurDisc protected media inside. Place the pointer over SecurDisc(TM) and then click Data Integrity Check.
The easiest way to check Data Integrity is simply to go to My Computer and right click on the drive with the SecurDisc protected media inside. Place the pointer over SecurDisc(TM) and then click Data Integrity Check.Checking the disc
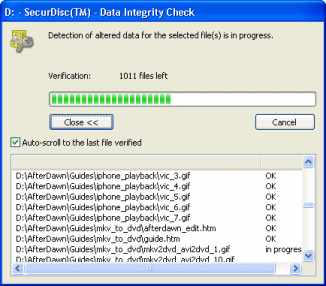 The application will now check every single file on the disc one by one, therefore, the amount of time this takes depends on how much data you have stored on the disc. Bigger files take longer obviously.
The application will now check every single file on the disc one by one, therefore, the amount of time this takes depends on how much data you have stored on the disc. Bigger files take longer obviously.No Altered Data?
 What you hope to see here is "No Altered Data Found". This way you know that the disc is still healthy and it hasn't been somehow damaged. You should perform these checks manually on a regular basis with all of your SecurDisc protected content.
What you hope to see here is "No Altered Data Found". This way you know that the disc is still healthy and it hasn't been somehow damaged. You should perform these checks manually on a regular basis with all of your SecurDisc protected content.Final Thoughts
 Considering SecurDisc has not been available for a very long time, it is a welcome product from Nero AG and Hitachi-LG Data Storage for both business and personal use. If this guide taught you anything it should be that once you have walked through all the features of SecurDisc once, it isn't hard to protect your disc in any way available from then on.
Considering SecurDisc has not been available for a very long time, it is a welcome product from Nero AG and Hitachi-LG Data Storage for both business and personal use. If this guide taught you anything it should be that once you have walked through all the features of SecurDisc once, it isn't hard to protect your disc in any way available from then on.
Of course, other options do exist for data security. For example, password protection can be achieved with .RAR archives, and even though it is a software based solution, it is still pretty strong. SecurDisc's password protection would be vulnerable to the same kind of attacks that hit most other forms of password protection, brute force and so-called Dictionary attacks. However, the minimum of 16 characters make the likelihood of either of these attacks being successful very slim.
The option to use a Digital Signature adds an extra layer of security that could be useful much more for business use (where an individual may attempt to copy and alter a disc) more so than for personal use. When it is used, it is not a nag and running a check with a Public Key is not a necessity. If it is the only form of SecurDisc protection that you choose besides the mandatory features, it is like the Digital Signature check doesn't even exist until you need it.
Whatever way you look at it, making a hardware-software solution for data protection on writeable media was a good move, as it removes a lot of security concerns when backing up sensitive information to blank media. The price of the LG drives that support SecurDisc are also nice and low and affordable to all. Above all though, credit has to be given for how easy it is for an end-user with not much experience in data protection to utilize strong forms of security. Hopefully SecurDisc will bring piece of mind to many.
Finally
I really hope that you have enjoyed reading this document, whether as an instructional guide for you to get used to your own SecurDisc hardware, or as a review that will help you to decide if you want to invest in this technology. If you want to discuss SecurDisc further, you are welcome to do so in our Discussion Forums.
Version History
v1.0 - Nov 14th, 2007 by Dela -- First version published.
Written by: James Delahunty

