How to remove a TDSS (Alureon, TDL) rootkit
 If you are infected with a rootkit/malware from the TDSS family you might be having trouble removing it with traditional anti-virus programs. That's because these illusive pieces of malware are capable of hiding and protecting themselves. This guide will show you to how remove the majority of the infections easily.
If you are infected with a rootkit/malware from the TDSS family you might be having trouble removing it with traditional anti-virus programs. That's because these illusive pieces of malware are capable of hiding and protecting themselves. This guide will show you to how remove the majority of the infections easily.What do I need?
Firstly, you need to download a program called TDSSKiller from AfterDawn. TDSSKiller is developed by Kaspersky and distributed for free. It specializes in the removal of TDSS rootkit infections, though it can remove many other rootkits that use particular means to hide themselves within a Windows operating system. It can also remove bootkits which use the boot sector.
Download: TDSSKiller
What is a rootkit?
A rootkit is a form of malware that buries itself deep within the operating system in order to avoid detection and/or removal by anti-virus products. Rootkits can use a variety of means to hide themselves and protect themselves, such as manipulating low level system calls and subverting standard OS functionality.
It can hide its presence while running in memory, and hide the presence of the files on the HDD from Windows Explorer. It can even make Registry entries unreadable and inaccessible using methods such as null values, which cannot be displayed by Registry editing software.
A rootkit will often attack installations of security products on a Windows machine, and will block all Internet traffic to the websites of security firms or to Windows Update. Through contact with servers, rootkits can download updates or changes for itself or even download completely different malware or other products (such as Fake anti-virus scams).
What is Alureon/TDSS/Tidserv?
It is a family of data stealing trojans. The symptoms of an infection vary based on what iteration of the malware is present on the system, but all pick through network data and other areas to steal information which can then be sent back to servers.
The malware can be hard to remove using security software due to the lengths it goes to to protect itself. It infects low level system drivers to protect its rootkit from full detection and removal.
TDSSKiller
Kaspersky's TDSSKiller has some great things to offer if you find your computer infected with this type of malware. It is light-weight scanner that provides a graphical user interface (GUI) for ease of use. It will check installed Services and Drivers, and check the Boot Sectors of your hard disk drives for anything out of the norm.
It can remove many rootkits quite easily, cutting off the head of the malware infection (and killing the reason why it just seemed to come back every time you cleaned your system.) It can't fix everything of course, but its a very powerful tool to have.
You should run this tool as an Administrator on Windows Vista and 7.
TDSSKiller Scan
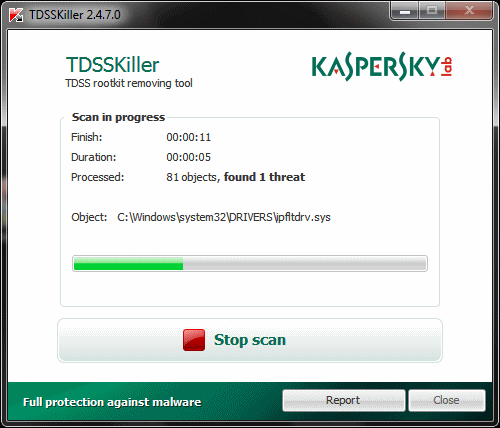
Clicking Start Scan will get the process going. The software will check through driver files for evidence of infection, or drivers / services that are suspiciously hidden. It will also check the boot sector for evidence of a bootkit, which it will be able to clean up in most cases.
Depending on how badly infected a system is with malware, the scan may take some time to complete, but on most systems it really should only take a few seconds.
Results
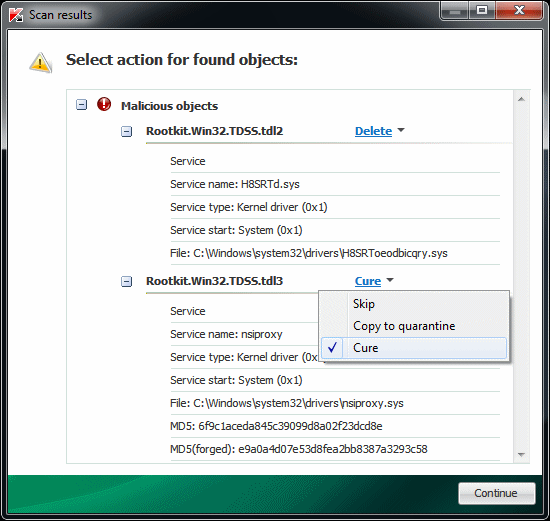
TDSSKiller will show two different types of results (if any), Malicious and Suspicious.
Malicious Objects: These results are malware that has been identified and confirmed by the tool. It could be an infected driver or a malicious service installed on the machine. In the example picture above we see results of two services, identified as Rootkit.Win32.TDSS.tdl2 and Rootkit.Win32.TDSS.tdl3. These are very serious results.
Suspicious Objects: These objects are unknown. They could be malware but in some cases they aren't. One example is sptd.sys installed with Daemon Tools, which is completely legitimate but shows up as a Suspicious Object because it fits the bill in one way or another. These results could be a hidden driver or service on the system, often the sign of a rootkit.
What action to take?

For Malicious Objects, TDSSKiller will automatically select either Cure or Delete. In the case of an infected (yet vital) system file, TDSSKiller may choose to Cure the object, whereas a hidden driver or service that is entirely malware may be selected automatically as Delete.
For Suspicious Objects, the default action to be safe is "Skip". One thing you can do here is Quarantine an object so it is not deleted. It will be saved to the C:\TDSSKiller_Quarantine\ directory. You could now scan this directory with an anti-malware product to see what result you get, or even better, upload the suspicious file to VirusTotal to see results from a wide variety of A/V engines. You can also decide to delete an object if you wish.
To change the Action, simply click the blue action test shown beside the result (in the example picture it was Delete and Cure.
Reboot
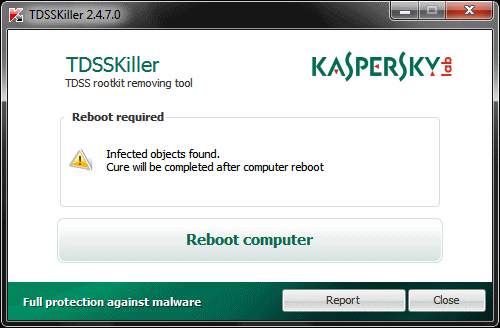
The last step of a removal process is to reboot the computer, as you will be prompted to do so. A logfile is created by TDSSKiller in the root (C:\) directory on your computer.
Written by: James Delahunty

