 TorrentPrivacy is a new product from the guys at Torrentreactor.net designed to keep your BitTorrent downloads and shares private. The product is a combination of an SSH tunnel tool, a pre-configured uTorrent client and remote privacy services. We'll take a quick sneak preview into how does it actually work.
TorrentPrivacy is a new product from the guys at Torrentreactor.net designed to keep your BitTorrent downloads and shares private. The product is a combination of an SSH tunnel tool, a pre-configured uTorrent client and remote privacy services. We'll take a quick sneak preview into how does it actually work.
After registering yourself at TorrentPrivacy.com you'll be able to download the 1 Mb installation package. Installation directory cannot be changed from the default "c: orrentprivacy" but I'm sure there's a reason behind it. After couple of clicks through the installation you are presented with the one click setup. After few seconds of connecting with TorrentPrivacy servers a Launch button appears and you're ready to go.
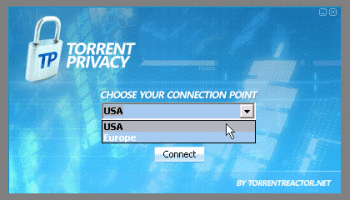
TP and uTorrent:
With a quick look into the client's preferences, you can see that the default download folder has been set to "c: orrentprivacydownloads" and Connections tab is a bit simplified, but that's about it. No additional setup was required and the v1.7.7 uTorrent was just what I've been used to.
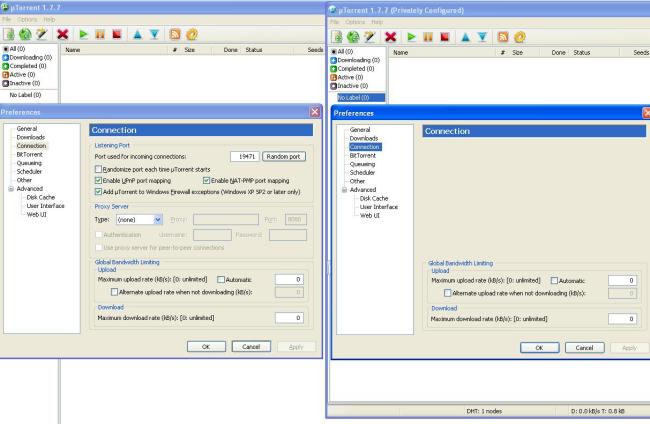
All traffic created by the privately configured uTorrent client are now being transferred through a secure SSH tunnel which encrypts all the data. You don't need to install any other BitTorrent clients and in fact TorrentPrivacy does not support any other clients. Additional proxies aren't required as TorrentPrivacy provides you with one to cloak your IP address. According to TorrentPrivacy they do not store traffic logs or other private information. The only sign of TorrentPrivacy running behind your uTorrent is the tray icon pictured below.
Conclusion:
Trying the software out myself it seems like a good, simple solution for ensuring your peer-to-peer privacy. Installation doesn't take more than half a minute and no configuration is required. With up to 100 Mb/s speeds it is also fast enough for pretty much everyone. Unfortunately it is currently only available for Windows users.
TorrentPrivacy is now offering 50% off from both one month ($9.95) and one year memberships ($99.95) registered during August. If you are not convinced, you can also get a one week trial for $2.95. If you have also tried the service or otherwise have opinions about it feel free to comment.











