TDSS
TDSS refers to a family of rootkits that target Windows operating systems.
TDSS rootkits are identified with many different names such as Alureon, Tidserv and TDSServ. The first rootkit of its kind was discovered in 2006, usually delivered when a Windows user unknowingly installs trojans from the web. It is often bundled with rogue security software (FakeAV products) as well.
Like other rootkits, it infects low-level system drivers in other to establish itself on the machine. From there it has been used for many illegal purposes, such as mining for data like credit card numbers, user names, passwords and other information that can be pulled from network traffic.
In order to protect itself, TDSS rookits generally block access to websites offering security products or updates for security products. They also block access to Microsoft's Windows Update service, protecting itself from the Malicious Software Removal Tool (MSRT) and also making sure an infected machine cannot be patched automatically against emerging vulnerabilities.
One incident in 2010 involving a TDSS rootkit made the headlines. Microsoft had pushed out an update that changed a hard-coded memory address that the rootkit used, and the result for the end user was an infamous Blue Screen of Death (BSOD). The Windows Update service will no longer deliver this update for systems infected with the rootkits.
The malware is used in the establishment of botnets, with Microsoft identifying it as the most prevalent of its kind in the area.
In June 2011, it was reported that the TDL-4 rootkit of the TDSS family had evolved to infect 64-bit versions of Windows (including Windows 7) by bypassing the Windows kernel mode code signing policy. It also its own anti-malware measures against rival malware such as ZeuS, Gbot and Optima, removing those infections from systems it compromised.
Another big leap for TDL-4 was to use the Kademlia P2P file sharing network for communications between infected nodes. This means a botnet it established can stay alive even if the command and control servers have been taken down through a legal route. In just three months, TDL-4 is reported to have infected over 4.5 million PCs.
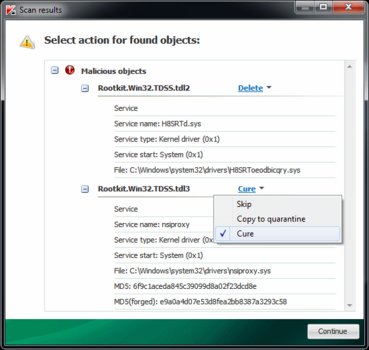
Tools such as TDSSKiller can be used to detect and remove rootkits / bootkits from the TDSS variants.